Cryptography Counters File Integrity Attacks.
In the previous article we summarized the vulnerabilities that can affect the computing infrastructure. For educational purposes, we have grouped these generic vulnerabilities into three:
Integrity.
Confidentiality.
Authenticity.
In this second article we will explain what tools cryptography offers us to defend the integrity of a file.
Integrity Attack
It refers to the elements messages, data, documents and other forms of content are intentionally or unintentionally altered by an external or internal agent. Solution: the cryptographic hash256 function.
How does the hash256 cryptographic function work?
A cryptographic hash function - usually referred to as a "hash" - is a mathematical algorithm that transforms any arbitrary block of data into a new string of characters with a fixed length. Regardless of the length of the input data, the output hash value will always have the same length.
There are many hash functions, but we will take the most widely used, the 256 hash, also called Sha256 (Secure Hash Algorithm), which takes any block of data and generates an output of 256 bits or 64 alphabetic and numeric characters (each character equals 4 bits), in the following examples we will use the online site that generates hashes: https://emn178.github.io/online-tools/sha256.html
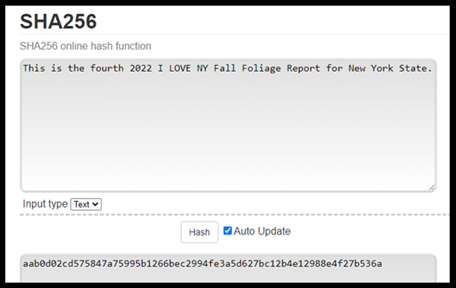
Example one. - We have the expression:
This is the fourth 2022 I LOVE NY Fall Foliage Report for the state of New York
We get the hash256:
aab0d02cd575847a75995b1266bec2994fe3a5d627bc12b4e12988e4f27b536a
This hash has sixty-four alphanumeric symbols.
Example two. - We have the expression:
This is the fourth 2022 fall foliage report from I LOVE NY for New York State. The reports are obtained from volunteer field observers and reflect the expected color conditions for the upcoming weekend. The reports are published every Wednesday afternoon.
We get the hash256:
f45c595e78da47910b64c0c4cf9b93a42ae7f686b8bbc1d72227c1cffabb44bd
This hash has sixty-four alphanumeric symbols, just like example one. No matter the size of the paragraph, the result has sixty-four alphanumeric symbols.
Hash256 Function Sensitivity
In the following examples, the hash256 function detects any change or alteration. Below, we have three expressions and their corresponding hash:
1. Life is beautiful
be03b1ef8d99a4be25895d376eb311fa484acae61c4ec182353b3d7135738ccb
2. Life is Beautiful
4f317a4065365d56de162b7872818900e70a60922b463722dec9081970e77aa0
3. life is beautiful
6536bba976b1491e19ca7f2dd865912bf6178240425bc3e23bfb5349273280ea
Observation:
In expression number two one letter changed, the lowercase b of beautiful for the uppercase B, the second hash is completely different from the first.
In expression number three, the uppercase L of Life changed to the lowercase l and the hash is completely different from the first and second.
File Integrity Protocol
Step 1: When saving a file, it includes the corresponding hash256 as metadata.
Step 2: Any unauthorized user can only access the file in Read Only mode.
Step 3: Only users who administer the computer system will be able to access Write mode. Authorized users must have a password.
Step 4: Implement some of the tools that generate hashes, in the programs that manage the computer system, examples of Programs to generate hashes (free):
Conclusion: If I have a program that when saving each file includes its respective hash256 (hash A). If an unauthorized user uses the file:
He will only have read access (Read Only), there is no alteration.
If he manages to modify it (through a cyber-attack), when trying to save it, the program recalculates the hash256 (hash B):
If hash A is different from hash B
The program will not allow you to save the changes. In the following articles we will study how cryptography defends us from the other two generic vulnerabilities.